Body language is defined as the non-verbal communication between two individuals or a group of individuals through physical behaviors such as limb movements, facial expressions, eye movements, other bodily gestures and postures.
Today, the term has assumed so much importance and prominence in all spheres of life that without a positive body language, none of us can survive in the professional arena, personal lives, and in the world, in general.
Body language comes into picture not only during normal conversations, but also during formal discussions, interviews, group discussions, panel meetings, etc. Proper body language not only conveys the right message to the recipient, but also attracts or repels the recipient.

For example, you are facing a job interview and the interviewer is questioning you. Now, although you are polite and replying well to the questions, the interviewer may still not select you. The reason is very simple. Perhaps your body posture or body movements were not appropriate or were rude. This may have led the interviewer to think that you are either not interested, or you are not a good candidate for the job profile.
However, body language is different from sign languages. In sign language, words or information is conveyed voluntarily using hand and finger movements. In sign language, mostly lip movements, finger movements, palm movements and eye movements are used to convey information to the recipient of the information. However, body language is different from sign language in the fact that body language is largely involuntary and is not actively controlled by the mind. However, sign languages are voluntary and are controlled by the mind to convey information.
What is Body Language?
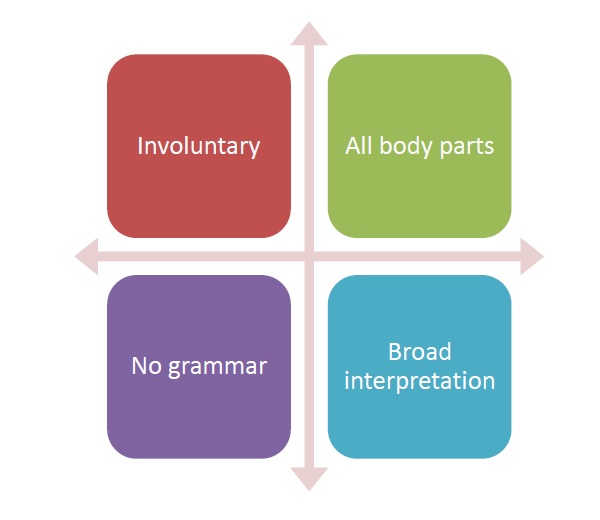
Following are the important features of body language −
It is a set of involuntary actions of the body parts.
It involves movement, especially of the limbs and the head.
It does not have grammar.
It has to be interpreted broadly by other people.
What is Sign Language?
Following are the important features of sign language −
It is not the deliberate movement of body parts to convey information. It is hence, not a voluntary action of body parts.
It has its own grammar.
It has absolute meaning, instead of subjective meaning.
However, this does not mean that if body language is involuntary, it cannot be controlled. By practicing certain techniques mentioned in this tutorial and through careful evaluation of one’s body movements each time, one can improve one’s body language easily.
Body language is quite particular to a specific culture. What is accepted in one culture may be a big ‘No’ in other cultures. Hence, body language is not universal and can be ambiguous too. This tutorial will teach you the essentials of good body language.
What is a Positive Body Language?
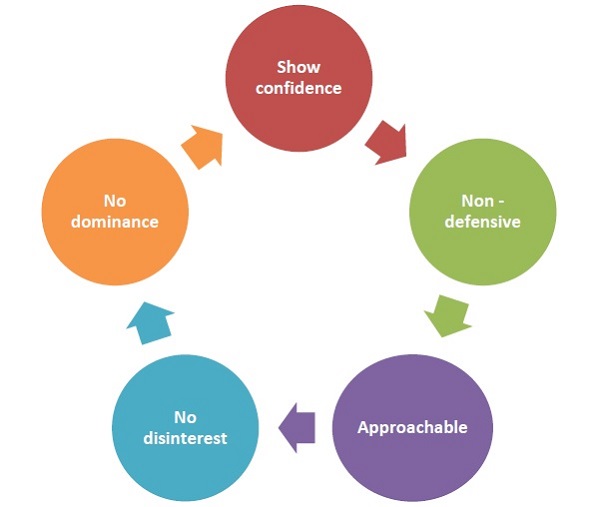
People find positive language appealing, receptive and easy to confront. A positive body language must place us in a position of comfort, dignity, and likeability. It helps us to be open to other people and be approachable, helping them feel comfortable when they are interacting with us. If our body movements somehow convey the opposite, then our body language is not positive and hence, needs to be improved.
Body language must not be defensive. Defensive body language discourages people from approaching us and establishing a connect with us.
Body language must not display a sense of disinterest towards the other person, as it can lead to failure in jobs, interviews and high-profile meetings.
The body language of a person must neither be authoritative nor submissive, but assertive to put forth our opinion and stance confidently without meaning any offence to the other person.
Positive body language helps people to be liked by other people in an organization or community and is therefore must for people across disciplines and ethnicities, as it plays a pivotal role in shaping our discussions and relationships with other people in our daily life.
Positive Body Language - Importance
Body language is of utmost importance in this highly competitive world. The corporate sector values good body language a lot and any sign of bad body language can break deals, even leading to loss of network for people.
An old adage says “Actions speak louder than words". Our body posture, along with its movements and placement of different body parts, play an important role in letting out our feelings and emotions, even if we don’t display the emotions voluntarily.
Assertive Behavior
A positive body language helps the person to be more assertive and assists in putting his or her opinion forward more easily than the others. Positive body language is liked by other people and hence, the person carrying a positive body language gets more attention and favor in any discussion.

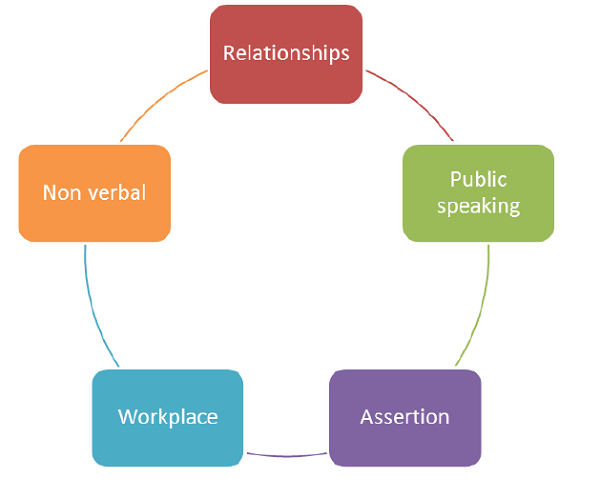
Non-verbal Communication
Research says that our communication consists of 35% verbal communication and 65% non-verbal communication. This implies that whatever we speak voluntarily comprises of just 35% of what the other person makes out of us. The remaining 65% information about us is learnt from our body language. Our body language helps others identify our emotions, status and even our lifestyle.
Non-verbal communication plays a significant role in conjunction with the spoken words. Our non-verbal communication can reiterate our message, contradict our words, reinforce our statement, substitute the meaning of our sentences and complement the meaning of our words. Since non-verbal communication can either emphasize our point or contradict it, it is necessary to keep our body language in sync with our emotions. Any sign of conflict between the body language and our words can make us appear untrustworthy and deceptive.

Workplace Success
Positive body language is a must in workplaces and corporate environment. Healthy body language can help foster team spirit in the workplace, which can also boost the morale of the employees. Delegation of responsibilities becomes easier through positive body language. It can also help in conveying respect for colleagues and resolving conflicts in the organization.
During corporate meetings, one can display interest, reception, and joy using positive body language. A gentle smile, open palms, leaning forward and eye contact can go a long way in establishing rapport with another person in the meeting thus helping build and sustain a healthy relationship with the other parties in a meeting.
Relationships
Negative body language can give way to a lot of misinterpretation and misunderstandings. Maintaining a body posture and absurd body movements that is offensive to the other person can ruin a relationship.
For instance, you need to understand the emotions and mood of the other person and need to customize your behavior accordingly. If your spouse is in a good mood, then it is okay to laugh or tease her occasionally. However, the same activity can be misinterpreted as sarcasm or irritable behavior if the spouse is not in a good mood. This can lead to issues between couples and can also lead to damaged relationships.
Public Speaking
In public speaking, body language assumes an altogether different importance. If the speaker has a defensive body language or has a passive body language, there are high chances that he or she won’t be listened to intently by the audience. The impact factor of such speeches also is reduced by a large fraction as the audience gets 35% of the entire communication but misses the remaining 65%. Hence, it’s highly important to have proper body movements and posture while speaking on stage in front of an audience.
Body language is very important in all forms of communication. It helps to break the barrier of unfamiliarity and helps to form a better connect with the recipient of information.
Good Standing Postures
Most of the times when we meet people, we are standing in front of them. Be it a casual meeting on the roadside or meeting someone in the office or having a conversation with a friend at a party, many of the conversations in our life happens in a standing position.
Following are the important postures to look for while standing and having a conversation.
Rule 1: Stand Erect
The first point to be kept in mind is to stand with the spine erect. The back must be straight as this gives an impression of being tall. A taller appearance creates good impression as well. You must not slouch or hunch.
Hunching or slouching gives an impression of laziness and lethargy. A person won’t like to approach you to talk if you appear to be weak or lethargic. Active personality is always preferred by people. Bad standing posture also symbolizes low self-esteem. This is not a good attribute to sport while standing.

Rule 2: Face the Person
The second point to remember is to not face sideways from your listener. Try to stand facing the person who you are communicating with. Standing sideways shows that you want to run away from the person and don’t want to continue talking. Watch out for the same signals from the other person as well. If that person is standing sideways, please stop the conversation as soon as possible. This is because the other person is not interested in the conversation.
The best way to stand is to direct your heart towards the other person. Ensure that your heart faces the heart of the other person without any obstruction in between. Standing with arms crossed over the chest is also a big ‘No’. It is better to stand akimbo or with your hands over your waist. Having crossed arms symbolizes defensive position or introvert nature. This type of attitude is seldom liked by people and it puts most of the people off.
Rule 3: Free Your Hands
The third point to be careful about is to not put your hands inside your pockets, while talking to someone. This posture shows disrespect. Keeping hands in the pocket shows that a person is not interested to talk. Remember that arms are the vocal chords of body language and can speak volumes about your attitude and interest.

Rule 4: Look into the Eyes
The fourth point to be careful about is to look into the eyes of the other person without intimidating him or her. If you keep looking away from the other person, it will show lack of interest in the conversation on your part. Keep looking for these signs in the other person too. Perhaps, the other person is looking away from you for most of the time. That will mean that the person is not engrossed in you and hence, it is better to let the person go.
Rule 5: Move, Yet Mind Your Limbs
Last but not the least; it is okay to have some limb movements. Moving hands to a certain extent shows your interest in the conversation and your excitement levels too. Don’t fret too much with hands, and try to keep your palms open. You should also stand with your legs apart. Don’t fiddle with your nose using your fingers because that symbolizes shyness and lack of confidence. Moreover, the legs must not be crossed. Crossed legs signify uncertainty and closed nature.
Good Sitting Postures
A lot of conversations happen while sitting as well. Job interviews, group discussions, or even candid talk with friends happen a lot while sitting in a restaurant, café or library. A lot of attention needs to be given to body language while having a conversation in the sitting position.
Rule 1: Face the Person
Always face towards the other person while speaking. Like in standing posture, here too, try to face your heart towards the heart of the other person. Don’t sit sideways unless necessary.
Also keep looking out for such signs in the other person. If the other person is sitting sideways for some considerable amount of time, it is better to drop out of the conversation as the other person is not interested.

Rule 2: Look into the Eyes
The second point is to maintain direct eye contact with the other person. Look into the eyes of the other person without intimidating him or her.
Rule 3: Mind Your Legs
The third point to focus on is the movement of legs. Since legs are far away from our eyes, we usually forget to keep the legs in check. Too much leg movement is not a good sign. Juggling of the legs show lack of interest in the ongoing activity and a longing to escape from it.
Rule 4: Don’t Slouch
The fourth point to take care of is to not hunch or slouch while sitting. During a job interview, don’t place your arms over the desk and don’t lean forward. The feet must be placed firm on the ground and must not be juggling at all. The spine must be straight and head must be held high. However, when you are having a candid conversation with friends, it is fine to place your arms over the desk and to lean forward. That shows your interest in what the other person is saying.

While sitting, avoid massaging your head, ears or forehead. Doing so signifies vulnerability and uneasiness.

Rule 5: Scream of Importance
While sitting during any conversation, don’t restrict your legs to a small space. Try to spread out your legs a little. It shows that you occupy some space and that you are in charge.
During group discussions, it is a bad gesture for a man to keep one’s legs crossed. However, ladies can sit with legs crossed without any issue. During interviews, it is preferred to sit with uncrossed legs as it signifies openness and acceptance.
The Proper Handshake
Handshakes are an indispensable part of our lives. Day in and day out, we meet friends and colleagues with whom we are supposed to shake hands. Handshakes are as old as the human civilization. In Roman times, the practice of lower arm grasp was followed as a way to check if the other person has concealed a dagger under the sleeves. Slowly, this converted to a form of common greeting and then, it eventually turned into the modern day handshake.
Shaking hands has a lot of Do’s and Don’ts. You should not always offer a handshake to a stranger. Handshake is a sign of welcoming people. If you are unsure whether you are welcome at one place or not, it is better to not go for a handshake. Salespeople can be observed taking care of this all the while they meet a new person. They resort to a simple head-nod rather than initiating a handshake. A handshake should not convey dominance or submission. What it should actually show is equality. Let’s take a quick look at some of the common handshake customs around the world and their features.
The Equality Handshake
Whenever you shake hands, it’s interpreted as a subtle symbolic power struggle between you and the other person. In short, the palm of either of those involved in the handshake must neither be facing down nor facing up.
For a proper handshake, the palms of both the individuals must be in vertical position. Then, both the people must apply the same pressure. If you find that the pressure you are applying is greater or lesser than the other person, then you need to modulate your pressure accordingly.

The Submissive Handshake
The submissive handshake happens when your palm in facing up and is below the palm of the other person. This is called “palm up thrust”. This makes you look submissive. Don’t let the other person get an upper hand at the handshake.

The Dominant Handshake
The opposite of submissive handshake is the dominant handshake. This happens when you place your arm above the palm of the other person and hence, your palm is facing down. This is called “palm down thrust”. This handshake conveys authority and dominance on your part. Don’t let the world think that you are submissive just because your palms are placed over the palm of the other person.

The Double Handler Handshake
When a person presents you with a palm down thrust, respond with your hand in the palm up position and then apply your second hand to make his palm straight. It is considered to be one of the most powerful handshakes in the world as it symbolizes sincerity and a strong bond between the two people involved in the handshake. This handshake is also called as the politician’s handshake, since politicians use this type of handshake a lot.

The Wet Fish Handshake
This is one of the worst handshakes in the world. In this handshake, the hands are cold and sweaty. This is perceived as a weak handshake and the person giving such a handshake is considered to be of weak character and to be lacking commitment.

The Vice Handshake
The vice handshake is another much loathed handshake around the world. This handshake is done by a palm up thrust and then a stronghold of the other person’s hands followed by vigorous hand movements. The strokes are so hard that it appears the person giving such a handshake is too authoritative and dominant.

The Bone Breaker Handshake
In the bone breaker handshake, the person giving this handshake grips the hand of the other person and grinds it with his hands. This handshake signifies aggressive personality and should not be used at all.

The Fingertip Handshake
One of the most hated types of handshakes is the fingertip handshake. In this type of handshake, the two people merely touch the fingertips of each other and give a very slight stroke or may even miss the stroke. This handshake conveys lack of confidence and lack of self-esteem. This is a handshake observed many a times during job interviews. Even before the interview begins, this type of handshake puts off the interviewer and the interviewee’s impression goes for a toss.

The Straight Finger Handshake
In this type of handshake, the person giving the hand has all his fingers straight. It is a very bad and rude gesture not to clasp the palm of the other person, as it shows lack of interest in the meeting and repulsion towards the other person. Always remember to clasp the hands of the other person during a handshake and give it a proper stroke.
Important Tips
It should be noted that after giving a handshake, one should not hold or touch the arm of the person with the other hand. It is a mark of patronizing, which is not seen in good light by people across the world. Only people who are at a higher authority can do so.
One’s hands should not be sweaty or wet while giving a handshake. It is quite unprofessional and rude to have clammy hands while giving a handshake.
You should stand straight or you can bend a little to show respect while shaking hands. It is always to be noted that the palms and the hands must be vertical while giving the handshake, so as to signify equality.
Proper Hand Movements
Hand movements are quite involuntary in nature. However, they tell us a lot about the other person who is using his or her hands while talking. There are rules for positive body language even in case of movement of hands.
Rule 1: Open Your Palms
The first rule is to have an open palm always. Open palms signify openness and acceptance. Open palms also signify honesty and sincerity. However, there is a way to read the open palms as well. If the palms are open while talking but are faced downwards, it signifies a bit of authoritative attitude of the person. This is visible especially in case of handshakes, as we saw in the previous chapter.

However, if the palms are open and are facing upwards, then it is a non-threatening sign. This person is approachable and can be seen as friendly in nature. The turn of palms, hence, completely alters the way others perceive us.
Rule 2: Uncross the Arms
While speaking, the arms should not be crossed and the hands must not be clasped. Clasped hands show lack of commitment and lack of confidence. Crossed arms show defensive or nervous position. It has also been observed that if a person stands with his arms crossed, then he grasps much less of the conversation as compared to a person with open arms. Moreover, defensive body language also leads to lower retention power.

It is in our common nature to cross our arms so as to feel comfortable. However, studies have shown that such a body language is perceived as negative by people. Moreover, clenched fists are also a big no during conversations. The arms should not go below the waist level and must always be raised above the waist while speaking. The arms can occasionally go down but it should not be so throughout the conversation.
Rule 3: Don’t Grip Your Arms
While speaking to someone, don’t grip your arms by crossing them. It is a sign of insecurity. Always avoid holding your arms together in front of your groin area, as it shows insecurity as well. It is called the Broken Zipper position. This is one posture that shows insecurity and submission at the same time and hence, must be avoided at all costs.

Don’t keep adjusting your cuff links in the public as it again shows you are too much concerned about your insecurities of coming out in public. The ladies must make a note that they should not clutch their handbags close to themselves as they talk as it shows their defensive position and their insecure nature.
Rule 4: Zero Arm Barriers
When you are in a restaurant, don’t clutch your coffee mug close to your chest. There should be no arm barrier when you talking to another person. Keep an open body language and hold the coffee mug at a side.
Rule 5: Parallel Over Perpendicular
In group discussions, it is a mandate that if you have to point towards someone, don’t use the arm that will be perpendicular to them. Use the other arm that can point to them and can be parallel to your chest too. Having the arm perpendicular to your chest to point out to others is generally a rude gesture. Always try to have the arm parallel to the body.
Arms and hands have to be used carefully in conversations. The movement of your arms and hands can make or mar your discussion and can alter the outcomes significantly.



